

Jump to winners | Jump to methodology | View PDF
The onset of the COVID-19 pandemic pushed a profession that has been notorious for its sluggish adoption of technology to make a major shift in the way it operates. Across Australia, law firms and organisations had to make the decision to go digital very quickly to accommodate the need for remote work arrangements – not just internally, but in the way they coordinated with clients.
Cyber law skyrocketed in importance as the increased digitalisation across businesses in various sectors was accompanied by a spike in cyber-related concerns. Cyber attackers exploited system weaknesses resulting from the sudden transition to working from home, and preyed on people’s fears to bolster the effectivity of phishing attempts.
Major firms, such as Allens and Seyfarth Shaw, have fallen victim to cyber attacks recently, and the hack attack on US file transfer service provider Accellion also compromised the data of Jones Day. Ransomware has been determined to be the main cybersecurity concern businesses faced over 2020–2021.
Demand for legal advice in fields such as cybersecurity, data privacy and protection grew as businesses became increasingly aware of the risks surrounding the heightened use of tech. Companies also became more conscious of their changing cyber law obligations.

The cyber law evolution
While demand for cyber law advice was already growing prior to COVID-19, the pandemic drove up the success rate of cyber attacks, driving demand up even more.
“While cyber law and cybersecurity risk were already key issues to be managed for businesses prior to the pandemic (including in key supplier contracts), the pandemic has accelerated the use and reliance on information and communications technology,” MinterEllison partner Paul Kallenbach says. “This, in turn, has resulted in more data than ever before being collected and processed, as well as heightened cybersecurity risks and challenges.”
He adds that remote work arrangements have contributed to the new challenges encountered in the cyber law space.
“The pandemic-related cyber challenges stem, in part, from the significant increase in the number of employees working from home, with the attendant risk of ‘shadow IT’, ie unauthorised systems or services, being employed; insecure devices, such as insecure routers, being used; and IoT devices such as smart assistants being proximate,” Kallenbach says.
Wotton + Kearney cyber team leader Kieran Doyle points out that working from home has expanded the attack surface for cyberattackers.
“We have seen a greater vulnerability landscape as businesses began working from home almost immediately. Remote working has created a larger attack surface as people log into the office from home, either adding a vulnerable home network as a gateway into the work environment or hastily put-together remote working with open remote working ports left vulnerable to attack,” he says.
Cyberattackers have also been capitalising on the volatile atmosphere created by the pandemic.
“It’s not like the threat actors have doubled in numbers since the pandemic began. However, what we have seen is more successful attacks than we did before, leveraging off the feeling of uncertainty and perhaps more realistic phishing attacks using people’s thirst for COVID-19 information to their advantage,” Doyle says. Thus, he calls for law firms to “evolve with the continuing threat landscape”.
“Security of systems is now a vital part of operations for all law firms, and you certainly can’t remain static,” says Doyle.
MinterEllison has also responded to the heightened cyber risks by introducing what Kallenbach calls a “comprehensive cyber resilience strategy that aims to reflect best practice”.
“This includes regular staff training [to increase] awareness of evolving cyber risks and the critical importance of each person’s role in protecting against cyberattacks,” he says.
Common cyber law concerns
In the current environment, both large and small organisations have been increasingly victimised in ransomware attacks – something law firms have not been able to avoid.
“Ransomware has increased in prevalence during the last 18 months – attacks against big and small businesses,” Doyle says. “You could say that this is the second pandemic of the last 18 months, which the government and opposition are now looking to address.”
Kallenbach added that ransomware has been revealed to be the main cause of cybersecurity incidents in 2020–2021.
“Businesses are seeking advice on whether ransom should be paid, and the potential legal, reputational and other implications should they do so,” he says.
“The increased occurrence of ransomware with an exfiltration capability has also presented challenges for organisations across every sector of the economy. The threshold issue of whether to pay the ransom is challenging enough without the overlayed complexity of potentially stolen personal information.”
Kallenbach says awareness of the dangers of data breaches has also spurred clients to seek clarity regarding breach reporting requirements.
“Clients recognised that the use of new technologies and platforms involving the collection of additional and large volumes of data would create new risks, particularly when being considered under pressure with the need to implement new tools urgently,” he says.
“However, in the ensuing months, and with the number of data breaches continuing to increase, clients are increasingly seeking advice on their breach reporting requirements at law, including under the Privacy Act and pursuant to specific industry-based requirements, such as CPS 234 for APRA-regulated entities.”
Even though ransomware incidents are grabbing the headlines, Doyle cautions organisations against discounting the threat of phishing.
“Business email compromise is still a significant threat for businesses, leading to invoicing fraud,” Doyle explains. “We tend to see this pick-up in volume during busy times of the year, where targets are more likely to click through without questioning, say, a phishing email. It’s a simple yet very effective attack and one that businesses should prepare for just as much as ransomware.”
Kallenbach supports this view, noting that MinterEllison’s Perspectives on Cyber Risk 2021 report, revealed phishing emails to be the most common way cyberattackers went after companies’ data. He added that organisations have also become more conscious of their cyber law obligations.
“Our clients, particularly those in highly regulated sectors, have been seeking to understand their evolving cyber law obligations, and also ensuring that back-to-back requirements are appropriately reflected across their supply chain, particularly as they move towards procuring an increasing number of cloud services,” he says.
Legislative developments
As the profile of cyber law increases further moving forward, legislation is looking to catch up.
“A number of consultations are underway to reform Australian cyber laws. These include the Australian government’s recently announced consultation on options for regulatory reform and voluntary incentives to make Australia’s digital economy more resilient to cybersecurity threats,” Kallenbach says.
“This is an initiative of Australia’s Cyber Security Strategy 2020, and also aligns with the government’s critical infrastructure reforms and the current review of Australia’s Privacy Act. Following the outcome of these consultations, we will likely see law reform addressing the expectations for businesses to manage cyber risks, increased transparency around the security of technology products, and expanded legal remedies for affected organisations and individuals”.
Doyle believes that the law will evolve “at pace” with cyber challenges. “I am particularly keen to see some amendments to the Privacy Act to ensure the notification laws are made much clearer and fairer,” he says.
“I am also keen to ensure there is a balance to any refresh in cyber law. There is a lot of talk about enforcement and strict liability; however, I would really like to see the focus of any new laws to be on incentivising businesses, particularly small businesses, to improve their cyber and data hygiene”.
Doyle explained that it is not greater enforcement that stops cyber attackers, but rather, a strong defence and recovery strategy.
“Preparing business to be better equipped to repel and detect attacks and be able to bounce back quickly from them with minimal data and financial loss should be the focus, rather than punishment for experiencing an incident that is often unavoidable,” he says.
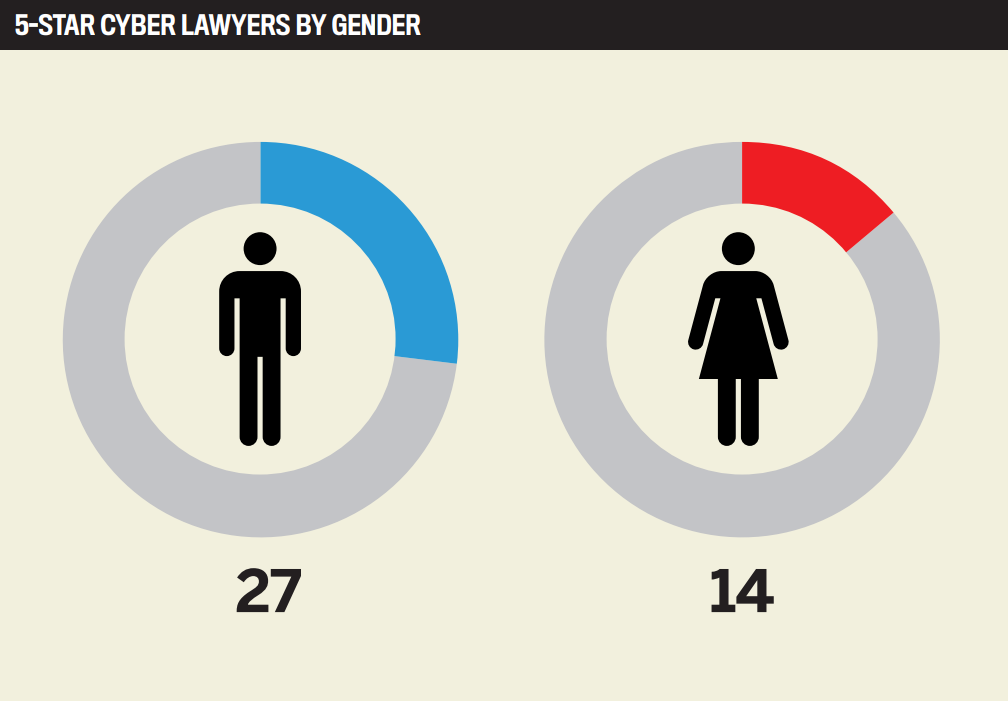
Australasian Lawyer’s first-ever 5-Star Cyber Law Firms and Lawyers list highlights the 40 lawyers and 27 law firms that have risen to the occasion as cyber law takes off. These legal talents stayed on the pulse of the market’s needs, and were well placed to tackle the novel challenges the new normal has created.
Over a five-week period that kicked off on 7 June, the Australasian Lawyer research team surveyed industry professionals and in-house counsel across Australia to identify the cream of the crop in Australia’s cyber law market.
The team conducted in-depth phone interviews with the respondents, and also obtained peer recommendations from lawyers. Candidates were ranked based on work quality, specialist expertise and client service quality.
The cyber law practitioners and firms that were awarded 5-star rankings by their peers were included in Australasian Lawyer’s inaugural 5-Star Cyber Law Firms and Lawyers list.
The 5-Star Lawyers were categorised according to the following specialist areas: cybersecurity, privacy, data protection, and technology (including media and intellectual property).
